We use many different applications, various portals and social networks on a daily basis and for many of them we choose (or are forced) to have an account. In order to reduce the risk of account getting hacked and personal information being leaked, everyone can start with an ordinary thing – credential security. The best way to protect your personal information is to use physical keys such as Titan Security Key, YubiKey or Latvian eID card, or usage of specific authentication apps on smartphones such as Microsoft Authenticator, andOTP, Smart-ID, Authy, etc. Backup codes should also be stored securely so that access is recoverable in case the authenticator is lost or breaks down. If the usage of physical keys or applications is not possible and we use the basic password for identity confirmation, we can protect our accounts and profiles by creating a strong password and changing it from time to time.
Continue readingAll posts by Kirils Solovjovs
Dynamic content in secure digital signatures
One of essential functions of digital signatures is to guarantee the integrity of the signed data. That is achieved by encrypting the data (its checksum) with one of the asymmetric cryptography algorithms. When you make changes to the signed data, the checksum no longer corresponds to the value included in the signature, so the signature can be identified as invalid.
However, in real life, the data to be signed is often far more complicated than plain-text strings. When digitally signing document files, it is only guaranteed that the binary content of the document file is exactly as it was at the time of signing. However, it does not say anything about whether the visual representation or the document contents in the applications displaying these documents is the same.
We are demonstrating a number of ways in which, by using various functions available in .docx and .odt formats, it is possible to create documents whose file contents are unchanged and thus are not raising any doubts about the validity of the digital signature, but in which the actual content displayed to the user may vary.
Continue readingGoogle CTF 2017
Some would say that this year’s Google CTF was harder than usual. Maybe it was. But it also was great fun.
Even though this was the first time possiblesecurity.com team participated in any CTF, we scored 79th place out of 1976 contenders worldwide.
Kirils also submitted a write-up for one of the challenges — JohnnyBoy — and now that write-up winners have been announced, we can publish it too.
Will we be back next year? Sure thing!
Vulnerabilities of Milesight IP security cameras
Internet of Things is becoming ever more popular, and vendors seek to capitalize on that: nowadays the manufacturing process of some security cameras is more alike to that of an Internet of Things device, rather than a security device. This reckless attitude undoubtedly leads to security vulnerabilities in critical systems.
Our lead researcher Kirils Solovjovs participated in IT security conference “Cyberchess 2016” jointly organised by CERT.LV and ISACA Latvia, where he presented his research on the security of Milesight IP security cameras. Multiple major security vulnerabilities were presented (CVE-2016-2356, CVE-2016-2357, CVE-2016-2358, CVE-2016-2359, CVE-2016-2360). The presence of vulnerabilities in the wild was verified in cooperation with CERT.LV by testing a Latvian public institution with more than 100 products by this vendor.
Given that vendor is located outside EU, Kirils initiated an international responsible disclosure process, working with the vendor, CERT.LV, the public institution, the installer, HackerOne Inc., and CERT/CC.
The presentation covers the technical aspects of vulnerabilities (presented publicly for the first time), lessons learned, and recommendations to security officers and policy makers. Video recording is also available.
MAKE RIGA Hacking competition 2016. Results.

Last weekend the Institute of electronics and computer science (EDI) hosted MAKE RIGA Hacking competition 2016, which is set to become a yearly tradition. Co-owner of 1st Ltd Kirils Solovjovs defended his champion title by attaining first place once again.
“The number and variety of challenges as well as the number of contenders is clearly increasing, providing for a lively competition. I was not originally planning to attend, but seeing the high response rate, I decided to give it a go and sign up for the competition on its second day. One could say that ending up at the top this year was a pleasant accident,” champion Kirils Solovjovs said with a smile.
This year the organizers had prepared 33 challenges – 57% more than the previous year – to wrestle with in the following categories among others:
- encryption,
- Internet of Things,
- WiFi security,
- social engineering,
- embedded device and microchip analysis,
- radio intercept and decoding,
- RFID security,
- reverse engineering software binaries,
- security of network services.
This year’s competition was well attended with 38 participants taking part from all around Latvia. Contenders included IT professionals, scientists and other interested parties.
The gold trophy was won by IT security expert Kirils Solovjovs who maxed out at 162 points. Krišjānis Stikāns was well behind with 99.5 points. Bronze trophy was awarded to Aleksandrs Levinskis for scoring 91 points. He was closely trailed by Dāvis Mosāns and “mkz” who scored 90 and 89 points respectively. Six of 33 challenges remained unsolved by anyone.
Cyber Europe 2016
 On 13th and 14th of October Possible Security took part in “Cyber Europe 2016” — the largest and most comprehensive EU cyber-security exercise to date. Cybersecurity authorities and cybersecurity experts from more than 300 organisations from all 28 EU Member States, Switzerland and Norway, reacted to a series of unprecedented, coordinated cyberattacks.
On 13th and 14th of October Possible Security took part in “Cyber Europe 2016” — the largest and most comprehensive EU cyber-security exercise to date. Cybersecurity authorities and cybersecurity experts from more than 300 organisations from all 28 EU Member States, Switzerland and Norway, reacted to a series of unprecedented, coordinated cyberattacks.
Exercise scenario included massive distributed denial of service attacks as well as disinformation campaign and sabotage of critical infrastructure, and featured the Internet of Things, drones, cloud computing, innovative exfiltration vectors, mobile malware, ransomware, etc.
Amongst the goals of the exercise was testing the ability of national and governmental cybersecurity agencies, ministries, EU institutions as well as internet and cloud service providers and cybersecurity service providers to safeguard the European Digital Single Market and creating recommendations to improve cybersecurity in Europe. After-action report will be made publicly available in the first half of 2017.
Exercise was organised by ENISA, the EU Agency for Network and Information Security. Possible Security is honoured to have been invited to participate in “Cyber Europe 2016” and be part of the solution together with our governmental and business partners.
First place at MAKE RIGA Hacking competition
 Institute of electronics and computer science (EDI) hosted the first MAKE RIGA Hacking competition last weekend. We are happy to announce that the co-owners of 1st Ltd Kirils Solovjovs and Jānis Jansons won the first and the third place respectively.
Institute of electronics and computer science (EDI) hosted the first MAKE RIGA Hacking competition last weekend. We are happy to announce that the co-owners of 1st Ltd Kirils Solovjovs and Jānis Jansons won the first and the third place respectively.
Contenders were given 13 hours over the course of two days to solve 21 challenges worth ten points each. Participants were competing in the following categories among others:
- WiFi security,
- password cracking,
- embedded device analysis, including firmware disassembly and flashing,
- radio intercept and decoding,
- RFID security,
- reverse engineering software binaries and hardware components,
- security of network services.
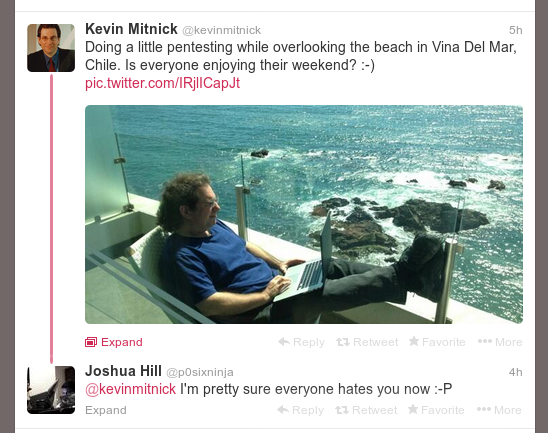
Getting rid of twitter in-line media
Chances are that you are a twitter user and while not using your mobile phone you are using the official twitter.com website. If not, you’re in luck, because recently they added quite a nasty feature that you can’t toggle on or off — the in-line media display.
Here’s a quick and clean hack to get rid of this nonsense.
- Install Stylish for Firefox or for Chromium.
- Restart your browser
- Click on the
 icon → Write new style → for twitter.com…
icon → Write new style → for twitter.com… - Add
div.tweet > div.content > div.js-media-container { display: none !important; }before the last bracket so that it looks similar to this:
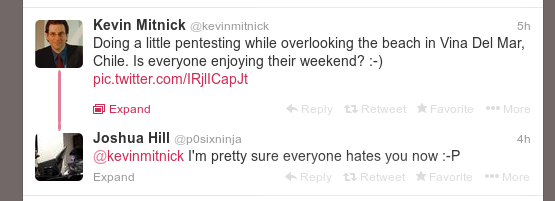
@namespace url(http://www.w3.org/1999/xhtml); @-moz-document domain("twitter.com") { div.tweet > div.content > div.js-media-container { display: none !important; } } - Click Save. The icon should turn
 and you should immediately be able to see the metamorphosis
and you should immediately be able to see the metamorphosis
Much better now, isn’t it? Enjoy your new and improved twitter on a sunny day over a beach! :)